Access Control
Learn how Deepchecks manages user permissions using role-based access control and how to assign and manage roles in your organization.
Overview
Deepchecks uses a role-based access control (RBAC) model with two tiers of access control:
-
Basic Tier (Default): Each user in the organization has a single role that applies to all applications in the organization. All users automatically have access to all applications.
-
Per-Application Access Tier: When enabled, each user still has a single role, but they only have access to a specific list of applications. Their role applies uniformly to all applications they can access.
Each user is assigned:
- A role (MetricsViewer, Viewer, Member, Admin, or Owner) that determines their permissions
- Application access (when per-app permissions are enabled) - a list of specific applications the user can see and access
Every role automatically includes all permissions of the roles below it, plus some additional capabilities.
Roles and Permissions
MetricsViewer
- Can view metrics and aggregated views
- Cannot access anything that contains raw data
Viewer
Includes all permissions of MetricsViewer, plus:
- Can view and access raw data
- Cannot upload data, create or edit properties, or change configurations
Member
Includes all permissions of Viewer, plus:
- Full write access to the application
- Can upload data
- Can create and modify properties
- Can update other configuration elements within applications
- Can create new applications
Admin
Includes all permissions of Member, plus:
- Can access Workspace Settings
- Can view, invite, remove, and manage users
- Can view and manage usage and billing-related information
- Can view organization-level logs
- Can assign roles and grant application access to users (when per-app permissions are enabled)
Owner
Includes all permissions of Admin, plus:
- Can manage additional system-level configurations with a dedicated Owner panel
- Can enable and disable platform flows and core features
- Can enable or disable per-app permissions for the organization
- Has the highest level of control within the organization
Application Access Control
Deepchecks supports two modes of application access:
Basic Tier: Organization-Wide Access (Default)
When per-app roles are disabled:
- All users in the organization automatically have access to all applications
- When a new application is created, all existing users automatically have access to it
- Users see and can access all applications in the organization
- A user's role applies uniformly to all applications they can access
Per-Application Access Tier
When per-app roles are enabled:
- Users only see and can access applications they have been explicitly granted access to
- When a new application is created, only the user who created it is automatically granted access. Other users need to be added by the Owner or Admins.
- A user's role applies uniformly to all applications they have access to
Managing Roles
Only Admin and Owner roles can manage user permissions within an organization.
Roles can be assigned or modified in two ways:
-
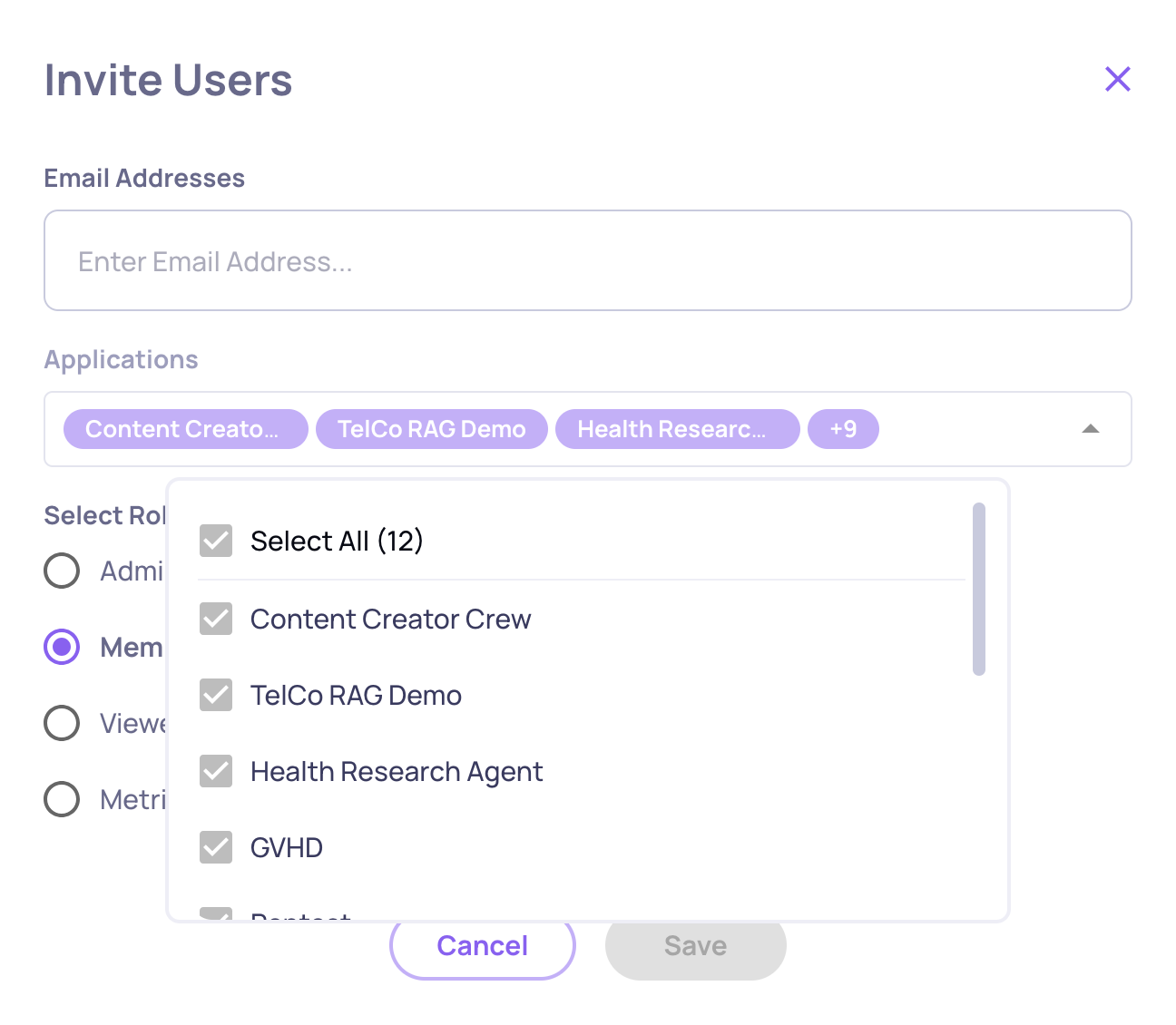
When inviting a new user - Admins and Owners can assign the user's designated role during the invitation process. When per-app roles are enabled, they can also specify which applications the user should have access to.
-
For existing users - Admins and Owners can change a user's role via the Users tab in Workspace Settings. When per-app roles are enabled, they can also modify which applications the user has access to.
Default Owner Assignment (AWS SageMaker & Self-Hosted Deployments)
In SageMaker and self-hosted deployments, the first user created in the organization is automatically assigned the Owner role.
This ensures that there is always at least one user with permission to:
- Invite additional users
- Assign roles
- Configure critical organization and system settings
- Enable or disable per-app permissions
Owner ChangeNote: Every organization must have at least one Owner at all times to manage configuration changes, invite users, and perform other administrative tasks. As a result, an Owner cannot downgrade their own role unless there is at least one other Owner in the organization.
Updated 10 days ago